
On April 11, 2025, the ground officially shifted under our feet.
In a move that has been rumored for years but dreaded by Operations teams everywhere, the CA/Browser Forum officially voted to pass Ballot SC-081v3. The decision is final, the clock is ticking, and the implication for every Platform Engineering team is brutal.
The era of the "Annual Certificate" is over.
Starting in March 2026, the lifespan of public TLS certificates will begin a rapid freefall from 398 days down to just 47 days.
The reaction across the industry has been a mix of denial and spreadsheet panic. "We barely manage renewals once a year; how are we going to do it every six weeks?"
This post breaks down exactly what the new timeline is, why manual governance is officially dead, and how you need to restructure your certificate lifecycle management before the first deadline hits.
1. The New Reality: From 398 to 47 Days
The reduction isn't happening overnight, but the "glide path" approved on April 11th is steeper than most enterprises can handle. Here is the official timeline enforced by the CA/B Forum:
- Today: 398 Days (~13 months).
- March 15, 2026: Cap drops to 200 Days.
- March 15, 2027: Cap drops to 100 Days.
- March 15, 2029: Cap drops to 47 Days.
The kicker: It’s not just the certificate lifetime. The Domain Control Validation (DCV) reuse period, the time a CA can "remember" that you own example.com , is shrinking to just 10 days by 2029.
2. Why Is This Happening? (The "Agility" Factor)
This wasn't a random decision. It was championed by Apple and Google with a clear security agenda:
- Crypto-Agility: If a cryptographic standard (like RSA-2048) breaks, they want the world to be able to switch keys in weeks, not years.
- Revocation is Broken: Certificate Revocation Lists (CRLs) are notoriously unreliable. Short-lived certs are the only true way to ensure a compromised key is useless quickly.
- Forcing Automation: This is the quiet part out loud. The browser vendors know that 47-day lifecycles are impossible for humans to manage. They are intentionally breaking manual workflows to force the industry into automation.
3. What This Actually Means for Your Team
If you are still tracking certificates in a spreadsheet or relying on calendar reminders, your process is now broken.
Let's look at the math. If you have 500 public certificates (a modest number for a mid-sized enterprise):
- Old World (398 days): ~500 renewal events per year. Manageable with a ticket queue.
- New World (47 days): ~4,000 renewal events per year.
That is an 800% increase in operational toil. If it takes a human engineer 1 hour to ticket, validate, approve, and install a cert, you just added 3,500 hours of busywork to your backlog. That is the equivalent of hiring two full-time engineers just to push the "Renew" button.
4. The "Hidden" Debt: Internal & Third-Party Certs
The announcement focuses on Public Trust (what Chrome/Safari accepts). But the ripple effect will hit your entire stack.
- Load Balancers & Ingress: Your NGINX controllers and ALBs need to reload these certs 8x more often. Are your reload scripts robust enough to handle that without dropping connections?
- Vendor Integrations: How many SaaS vendors (Salesforce, SAP, etc.) require you to upload a public cert for SSO or API verification? You now have to coordinate that manual upload every 6 weeks.
- Shadow IT: That marketing microsite deployed by an agency in 2023? It’s going to break 7 times a year now.
5. Breaking the "Reactive Firefighting" Cycle
This 47-day change is just the latest symptom of the Software Maintenance Tax.
Most engineering teams are trapped in a cycle of "Reactive Firefighting." You wait for the alert (or the outage), you scramble to fix it, and you go back to coding. With 47-day epochs, "Reactive" is no longer a viable strategy. You cannot react 4,000 times a year without burning out your team.
So, what is the path forward?
Option 1: The "Band-Aid" Automation (ACME Scripts) You can try to glue together Certbot, cron jobs, and bash scripts.
- Pros: Free.
- Cons: Fragile. Who maintains the scripts? What happens when the validation API changes? It’s just more "Glue Work" debt.
Option 2: Lifecycle Governance (The Draftt Way) You need to stop treating certificates as "Tasks" and start treating them as "Policy."
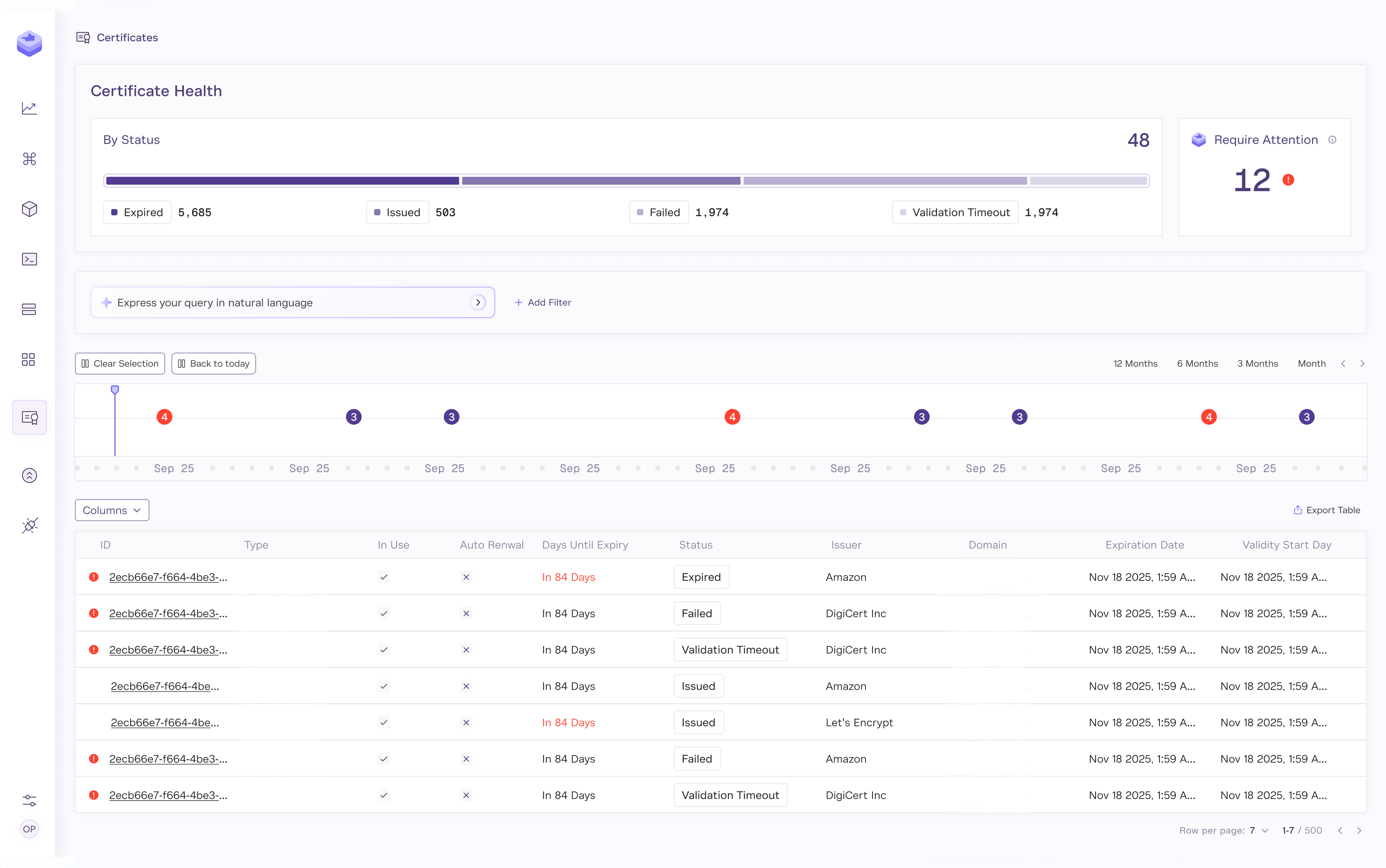
At Draftt, we view this through the lens of Proactive Governance:
- Discovery: You cannot renew what you can't see. We map every certificate, regardless of whether it's on AWS, Azure, or an on-prem NGINX box.
- Prediction: We don't just alert you on expiry. We identify the "Renewal Cliff" before it hits.
- Agentic Action: Instead of assigning a ticket to a human, the platform orchestrates the renewal itself.
The Bottom Line
March 15, 2026, is closer than it looks. The 47-day limit is a forcing function. You have two choices:
- Hire an army of engineers to manually manage spreadsheets and tickets (and watch them quit).
- Admit that Lifecycle Management is a job for machines, not humans.
The "Annual Renewal Party" is officially over. Welcome to the era of continuous maintenance.
Want to see how Draftt can automate your Certificate Lifecycle and end the renewal headaches? Get a Demo.

.webp)




.png)





